Your Digital Marketing Company Missing Users?
to take the traffic they’re leaving behind.






Innerly Digital
Marketing Solutions

SEO Writing AI
600+ posts a month.
Fully Localized.

AI SEO Services
+247.8% traffic in 4 months.
.avif)

Generative Engine Optimization

It’s Everything You Wish a Digital Marketing Agency Was

Connect Once

We Do the Work, You Watch It Scale

Users Start
Showing Up

Connect Once
We Handle the Rest


You Watch Growth

Who We Serve
Neo Banks
Skip the ads. We bring traffic that converts into deposits, not just clicks.
Stablecoins
Pegged to value, built for speed – we bring the search traffic that keeps your brand in motion and your protocol trusted.
Web3 Banks
Your chain-native bank deserves chain-level visibility, let’s go global.
Centralized Exchanges
The trading volumes there bring thebrand visibility to match.
Decentralized Exchanges
Your AMM deserves SEO that
scales – no gas, no downtime, just traffic.
Market Makers
Influence more than liquidity – dominate search and discovery too.
On-Ramp/Off-Ramp Solutions
Users need access. We make sure you’re the bridge they find first.
L1 Blockchain Networks
You built the foundation and we make sure the world finds it first.
L2 Blockchain Networks
You scale the chain, we scale your visibility to match.
DeFi Protocols
TVL doesn’t scale itself; we bring liquidity, attention, and authority.
Yield Platforms
Be the yield engine investors Google and AI platforms recommend.
Launchpad Platforms
You launch tokens, we launch traffic. Fast, global, unstoppable.
Crypto Payment Processors
From checkout to SERP-top we bring the merchants to your rails.
Blockchain Security
Protecting the chain? Time to dominate the trust game in search too.
Blockchain Auditing Firms
We help your audits rank higher than the breaches you’re preventing.
Crypto Tax
From regulations to rankings we make your tax tool the one users actually find.
Compliance Solutions
Complex doesn’t have to mean invisible – we make you searchable and simple
Oracles
Turn raw data into front-page results and be the source that search engines and AIs trust.
Data Providers
Got the numbers? We make sure you’re the one users see and cite first.
Research Platforms
From whitepapers to rankings we help your insights get discovered.
Crypto Media
Don’t just cover stories, own the narrative across search and AI.

Built for You, Proven by Results

247,8%

170

600+
Articles Monthly
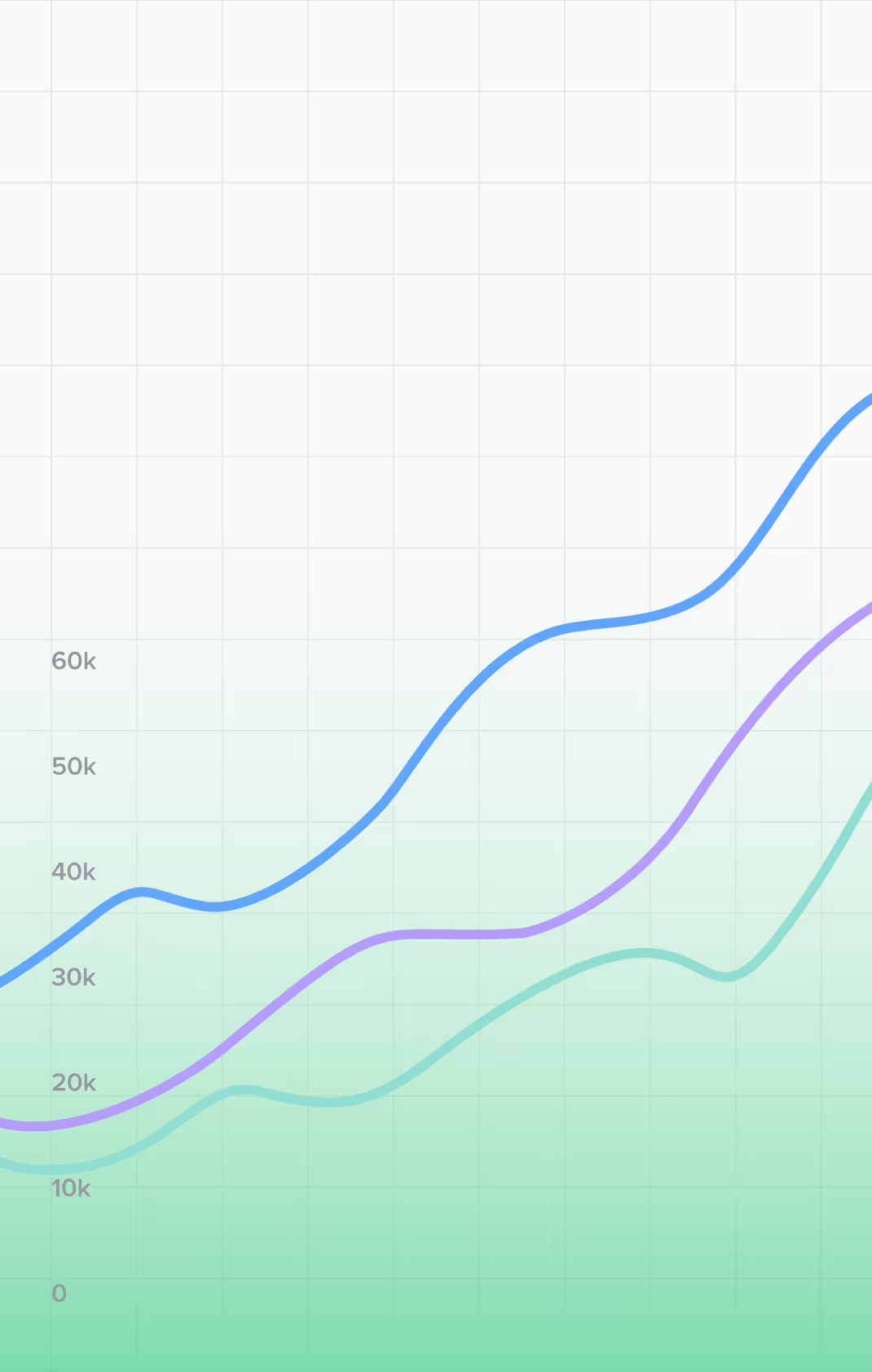
How OneSafe Scales Without a Traditional SEO Agency
Your Valuable Blog
Still wondering if Innerly is right for you?
What exactly does Innerly do?
Innerly gets you crypto users faster.
From AI Digital Marketing, SEO writing AI, and LLM Optimization, all in one-click.
How fast will I see results from SEO Writing AI?
Most clients see traffic lift in 2–4 weeks and major user growth within 90 days.No drafts. No approvals. Just done-for-you results.
Is Innerly just another SEO tool?
Tools give you tasks. Innerly gives you users.
Will it work for my crypto or fintech project?
Innerly has been built for DeFi, CEXs, wallets, L2s, NFT platforms, Web3 games, and fintech apps for anyone who needs growth without the grunt work.
Do I need a developer to set it up?
Set up takes one API. That’s it. No code. No dev time. No migration. Just go.



